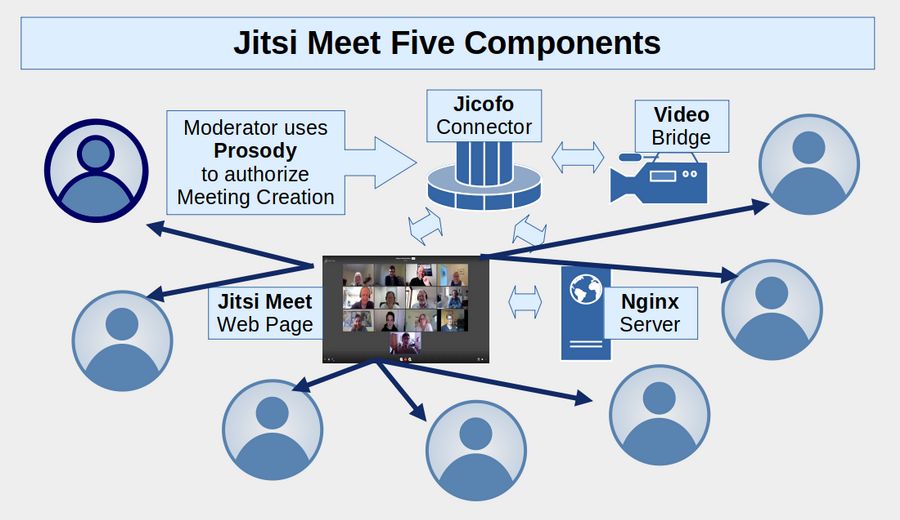
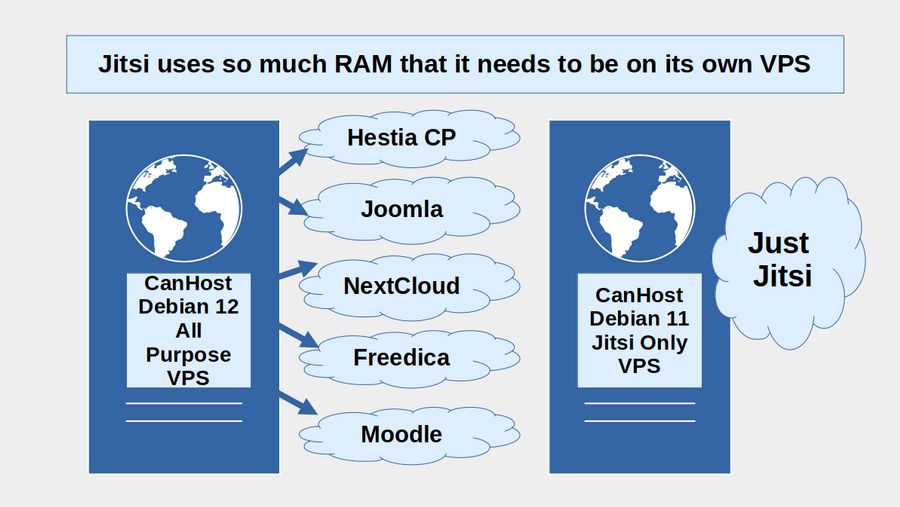
Video conferences are one of the most important ways to build relationships and organize political and social movements with others across the US and around the world. Jitsi is a free open source video conferencing tool that works on any computer. It does not require setting up an account or paying a monthly fee. By contrast, Zoom charges an annual fee that runs from $150 for a single user to $250 a year for a business. With Jitsi, you can add any number of people to your video conference and you can run your video conference for several hours for free rather than the 40 minute time limit imposed by the Zoom free account.
Why Jitsi is much more secure than Zoom
The biggest advantage of Jitsi is that it is dramatically more secure than Zoom. This is because moderators and participants do not need to download any “apps” to use Jitsi. Just open any web browser and go to your Jitsi video conference room. By contrast, to use Zoom, you need to download a closed source (and therefore insecure) Zoom app which has a file size greater than 142 MB. Extract the largest file and click on Properties for the two folders to see that the opt folder has 1,362 files and a total file size of 523 MB. Recently, Zoom increased the file size to over 800 MB. This means that Zoom is actually larger that the Linux operating system and about 8 times larger than a draconian Deep State program called UEFI – which itself is capable of remotely bricking any Windows or Apple computer.
To give you an idea of how large 800 MB is, the classic book called Moby Dick has 213,533 words divided over about 400 pages. It has a file size of about 1 megabyte. Thus the Zoom app is the equivalent of more than 800 copies of Moby Dick or more than 300,000 pages of code! Zoom has never explained what all the millions of lines of code actually do.
But the worst part is that nearly all of this code is hidden. It is not open source. It is not subject to an independent inspection or audit. This makes the Zoom app one of the worst pieces of malware ever written.
Requiring your participants to each download this app and placing it on their computer not only places your computer at risk – but also the computers of all of your students. Thus, even if Zoom was free, you should not use it or force others to use it.
By contrast, the code for Jitsi is entirely open source and therefore subject to public audits. These audits can and do confirm that there are no hidden back doors in any Jitsi programs. In addition, the file size for Jitsi as shown on their GitHub page is 135 MB meaning that it is only about 20% of the size of Zoom
Security researchers have called Zoom “a privacy disaster” and “fundamentally corrupt”. Arvind Narayanan, an associate computer science professor at Princeton University stated: “Let’s make this simple. Zoom is malware.”

Zoom has falsely advertised itself as using end-to-end encryption, a system that secures communication so that it can only be read by the users involved, a report from the Intercept found. Zoom confirmed that end-to-end encryption was not currently possible on the platform.
"We discourage the use of Zoom at this time for use cases that require strong privacy and confidentiality," the Citizen Lab report says, such as "governments worried about espionage, businesses concerned about cyber crime and industrial espionage, healthcare providers handling sensitive patient information" and "activists, lawyers, and journalists working on sensitive topics."